Proposed protocol simulation in presence of the intruder.
Par un écrivain mystérieux
Description

A review and analysis of secure and lightweight ECC‐based RFID

Simulation scenario for intruder detection application. Two
Analysing Security Protocols Using Scenario Based Simulation
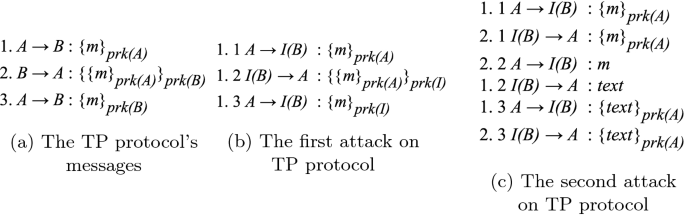
An attack on communication security (Intruder 1) and datasets

Cluster-Based Authentication Process in a Smart City

An example of replay attack on TAP initial authentication protocol
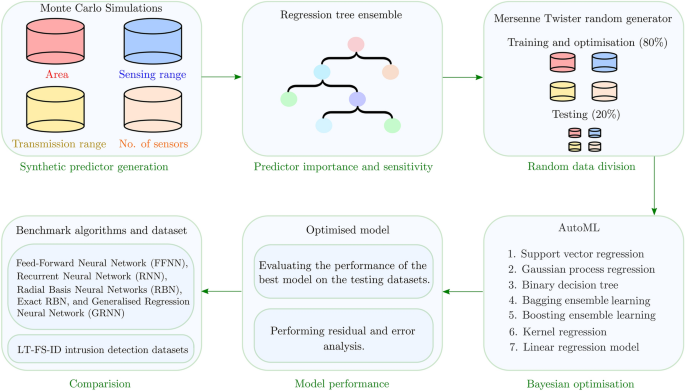
AutoML-ID: automated machine learning model for intrusion

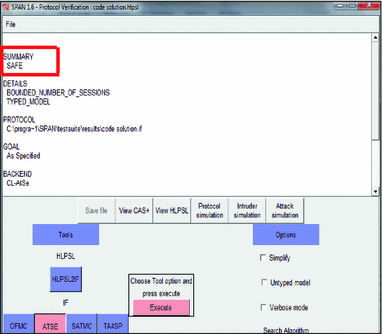
Intruder simulation of case 2 in AVISPA using CL-AtSe

A blockchain-based secure data-sharing framework for Software

Introduction into SkyRadar's Breach, Attack and Defense Simulator
ISEND: An Improved Secure Neighbor Discovery Protocol for Wireless
depuis
par adulte (le prix varie selon la taille du groupe)